Scale smarter. Automate faster. Find Applivery at RSAC 26.
Product
Key Features
Unmanaged Devices
Pricing
Pricing by Solution
Resources
Partners
Remotely manage eSIMs with full automation, from provisioning and configuration to deprovisioning. Scalable, secure, and perfect for modern IT teams.
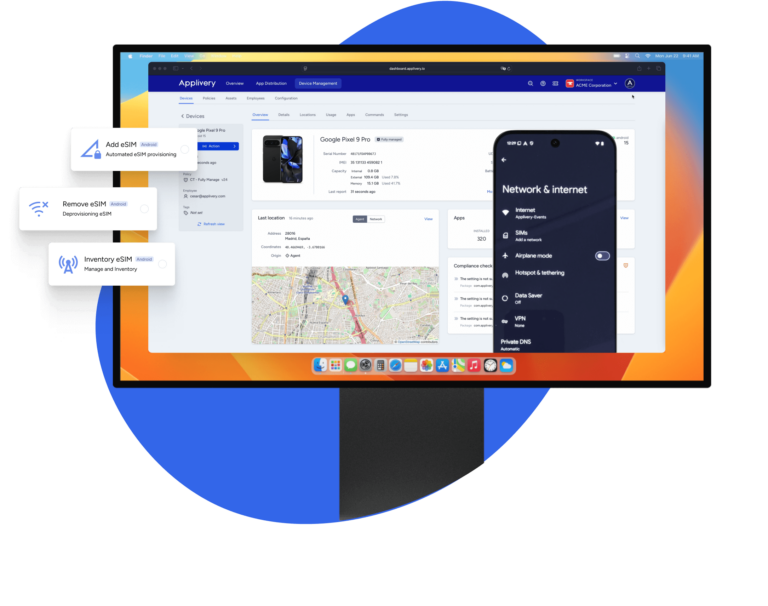
Easily provision eSIMs remotely with Applivery. Activate mobile connectivity on managed devices by simply adding an activation code. No physical SIMs, no manual setup, just fast, secure, and scalable eSIM deployment across your entire fleet.
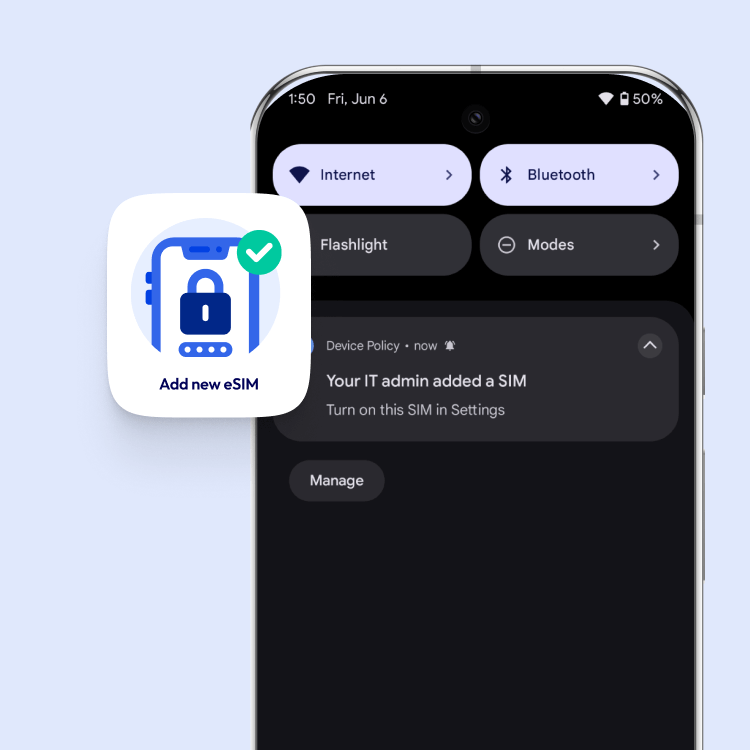
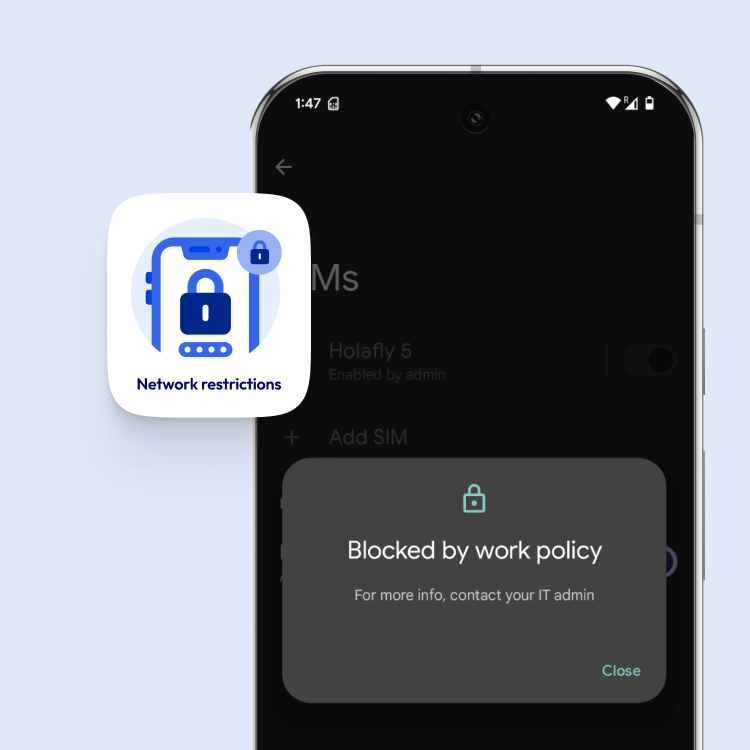
Restrict user access to mobile network settings with Applivery. Prevent changes to eSIM configurations and ensure policy compliance across all devices. Maintain control, enhance security, and reduce misconfigurations with just a few clicks.
Easily deprovision eSIMs remotely from any managed device. Remove connectivity instantly by targeting the ICC ID, no user action needed. Streamline offboarding, reduce risks, and keep your device fleet under control with secure, remote eSIM removal.

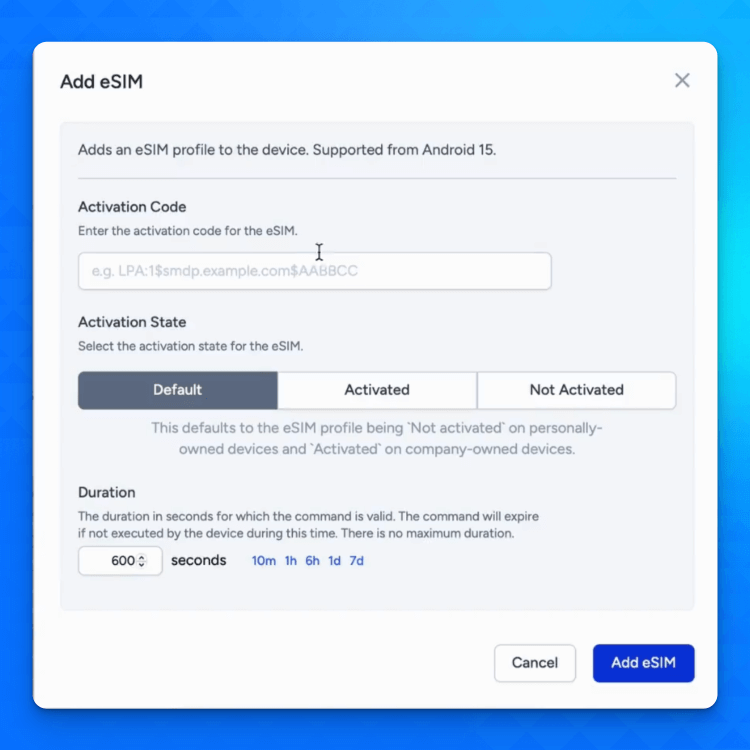
Starting with Android 15, IT admins can remotely provision eSIM profiles on managed devices using MDM/EMM tools. Applivery MDM solution (via Android Management API) allow admins to add eSIM profiles by providing an activation code and even enable them automatically on company-owned devices. This means organizations can push eSIM configurations centrally to many devices, eliminating the need for physical SIM cards.
Android 15 (API level 35) introduced official support for remote eSIM management. Both fully managed devices and company-owned work profile (COPE) devices running Android 15+ can have eSIMs deployed via MDM. Earlier Android versions do support eSIM at the OS level (many modern Android phones have eSIM hardware), but the ability for MDM to programmatically install/remove eSIM profiles is new in Android 15. Ensure the devices are eSIM-capable models (many flagship and enterprise phones in recent years support eSIM) and upgraded to Android 15 or later.
Enterprises will need to obtain eSIM activation codes or QR codes from their mobile carriers for each line of service, or work with carriers that support bulk eSIM provisioning. Typically, carriers provide a Subscription Manager (SM-DP+) server address and activation code for each eSIM plan. MDM software uses these to download the profile to the device. Some carriers allow pre-registering device EIDs (the eSIM chip ID) so that a device can automatically download its plan with minimal input. It’s important to note that not all carriers or countries fully support eSIM yet, so enterprise mobility teams should verify carrier eSIM support and any enterprise eSIM management offerings (like carrier portals or APIs for eSIM activation).
Android 15 introduced new admin controls to enforce eSIM policies. An IT admin can mark eSIM profiles pushed via MDM as “managed” so that on company-owned devices users cannot delete them. By setting the restriction DISALLOW_CONFIG_MOBILE_NETWORKS, admins can block users from removing an eSIM that the company installed. There is also a policy to “Disallow SIM globally,” which prevents the user from adding any new eSIM profiles on the device at all. In practice, this means IT can lock down a corporate device to only use the pre-approved cellular plan. (On employee-owned/BYOD devices, users will retain the ability to remove any eSIM profiles that were installed, see BYOD section below).
Partially. Admins can prevent users from adding their own eSIM plans by enabling the “disallow SIM globally” restriction, which blocks user-initiated eSIM downloads. They can also ensure that any eSIM pushed by IT cannot be removed by the user (DISALLOW_CONFIG_MOBILE_NETWORKS) on corporate-owned devices. However, blocking a physical SIM is not as straightforward, if a device has a physical SIM slot, policy can’t electronically stop a user from inserting a personal SIM. Some enterprises address this by using eSIM-only devices or by instructing users to avoid unapproved SIMs. Android 15 does note a new control to allow or disallow embedded vs. physical SIM usage on a device, which suggests admins may get the ability to disable the physical SIM interface or eSIM interface as needed. In any case, on fully-managed devices IT can hide or lock mobile network settings so users can’t alter connectivity without approval.
It depends on the platform and how the reset is performed. On iOS devices, for instance, MDMs can choose to retain the eSIM cellular plan during a remote wipe (ensuring the device comes back online with cellular). For Android, a factory reset will typically leave the eSIM profile intact unless the user or admin explicitly erases it. In fact, if a device is fully managed, an MDM-initiated wipe may preserve the eSIM so that the device can reconnect for provisioning after reset (though Android’s implementations are still evolving). Android 15’s framework treats managed eSIM profiles as separate from user data, so they should persist through a reset unless removed by policy. In any case, an admin can always re-push or re-activate an eSIM after a reset if the plan is still active. (Enterprise admins should consult their MDM documentation on whether a “wipe” command removes eSIM profiles or not, as this may vary by solution).
Yes. If the device supports eSIM, the IT admin can push a work eSIM profile to a BYOD phone (typically one enrolled with a Work Profile). Android 15 allows managed eSIM deployment even on personally-owned work profile devices. For example, a company could issue a business data plan via eSIM to an employee’s personal phone to avoid requiring a second device. The key difference is that on a BYOD device, the user will usually have to confirm enabling the eSIM, and they retain the right to remove that eSIM at any time. This gives flexibility: the employee can use the corporate plan when needed and delete it if they leave the company or no longer want it.
On corporate-owned devices, admins have full control: they can silently install an eSIM, activate it, and (with policies) prevent the user from removing it. On BYOD (personal) devices, the admin can install an eSIM via the work management app, but cannot enforce its presence long-term. Users on personally-owned devices will always have the ability to remove or disable the eSIM profile if they choose. Also, Android 15 introduced privacy safeguards for BYOD: the MDM cannot access details of the user’s personal SIM/eSIM profiles on the device. The corporate agent will only see and manage the enterprise eSIM that it installed. This ensures compliance with user privacy – IT can’t snoop on personal mobile plans or usage on a BYOD phone.
Absolutely. One of the advantages of eSIM technology is that it allows multiple plans on one device – for instance, an employee could have their personal line on a physical SIM (or a personal eSIM) and add a corporate plan via eSIM. The device’s dual-SIM capability (e.g. one physical, one eSIM, or even multiple eSIMs) means users can carry one phone for both work and personal use. Android lets users choose which SIM/eSIM to use for data or calls, so a work app could use the corporate eSIM for connectivity while personal apps use the personal SIM, if so configured. This dual-line setup not only is convenient but also helps in separating billing (the company pays for the corporate plan, while personal usage stays on the employee’s plan). It’s worth noting that the user must manage the SIM selection; Android doesn’t automatically segregate work vs personal data traffic by SIM. Still, having a dedicated work eSIM makes it easier to track and reimburse work-related mobile usage, supporting BYOD policies.
No. Android’s enterprise privacy model keeps personal data – including cellular subscriptions – segregated. With Android 15’s changes, EMM/MDM apps are prevented from accessing details of personal subscriptions on BYOD devices. The corporate agent can query and manage the eSIM profile it deployed (the “managed subscription”), but it cannot view the phone number, usage, or any info of the user’s own SIM/eSIM. This means IT cannot spy on personal call logs or data use from a personal SIM, which addresses compliance and privacy concerns. The admin’s control is limited to the work profile and any eSIM they provisioned for work.
When a device changes hands or an employee leaves, the IT team should remove any corporate eSIM profiles from the device. MDMs that support eSIM can send a command to delete the eSIM profile remotely. This de-provisions the cellular plan from that device – preventing further use of the company’s service. For device reassignment within the company, IT would remove the old eSIM (if the phone number/service is tied to the person) and then push a new eSIM for the next user or device owner. This process ensures the new user gets a fresh line and the previous user no longer has access. The removal can be done in seconds from the console, greatly streamlining device retirement or repurposing compared to chasing down physical SIM cards.
Yes. If a managed device is lost, IT has a couple of options: (1) Use MDM to send a “remove eSIM” command to wipe the cellular plan from the device. This cuts off its mobile connectivity (helpful if you’re concerned about unauthorized usage or data exfiltration). (2) Alternatively, contact the carrier to deactivate that eSIM line (similar to suspending service on a SIM card). Many MDMs also offer a full device lock or wipe; doing a remote wipe without removing the eSIM could actually help, since the device might then reconnect to cellular for a fresh provisioning. But for security, it’s common to disable the eSIM and lock or wipe the device. The goal is to prevent a thief from using the device or racking up data charges on the corporate plan. (On iOS devices, admins often retain the eSIM during a wipe to help locate the device; on Android, policies are evolving, but an admin-downloaded eSIM will stay unless removed, and you can always later disable it at the carrier level if needed).
Applivery is proud to be the first company in the world to showcase fully integrated Android eSIM management, including provisioning, configuration, and deprovisioning, live during the Google Pixel Manage Program event, created in partnership with Google.
The event, hosted at Google Spain, brought together key partners and customers, where Applivery demonstrated this groundbreaking capability in real time, solidifying our position as a pioneer in modern Android device management.