It’s a classic scene: you’re at the boarding gate and connect to the open airport free Wi-Fi. It’s an almost automatic gesture. But from an IT team’s perspective, every one of those clicks on an unmanaged network is a potential security alert. You have no visibility into its encryption, nor control over who else is “listening.” Multiply that risk by every employee who travels, and your security strategy becomes an exercise in crossing your fingers.
In this scenario, the answer isn’t to cross your fingers and hope for the best. The real solution is to replace uncertainty with certainty. This is where Applivery’s Wi-Fi Allowlist comes into play, designed to give you the ability to define a secure connectivity environment by default.
Open Wi-Fi: an all-you-can-eat buffet for cybercriminals
Let’s be clear: an unsecured public network is like shouting your passwords in a crowded square. Everything you send and receive travels without robust encryption, served up on a platter for any attacker on the same network to intercept. We’re talking about login credentials, corporate emails, confidential reports… everything is exposed. It’s the perfect playground for cybercriminals.
With an Allowlist policy managed through Applivery, you simply shut down that buffet. You set the rules and define which networks are trustworthy. For the employee’s device, all other networks become invisible. It’s not a recommendation; it’s an unbreakable technical barrier.

The trap isn't just technical: the double cost of "free" connectivity
The danger of these networks isn’t limited to a cyberattack. The business impact has two other facets that complicate your daily operations:
- Hidden costs
Many of these “free” networks are a facade. They redirect you to paid portals or consume mobile data at lightning speed, and suddenly, a spike appears on the company’s bill that no one can explain.
- Productivity down the drain
These connections are often slow, unstable, and frustrating. The loading bar that never moves, the video call that freezes at the worst possible moment… it’s not just an annoyance; it’s lost time and money for the company.
The Allowlist trough Applivery
By limiting connections exclusively to trusted networks, like the office’s or a secure mobile tether, the story changes completely. Implementing this policy makes you the company’s first line of defense. You stop putting out fires because you’ve prevented them from starting in the first place.
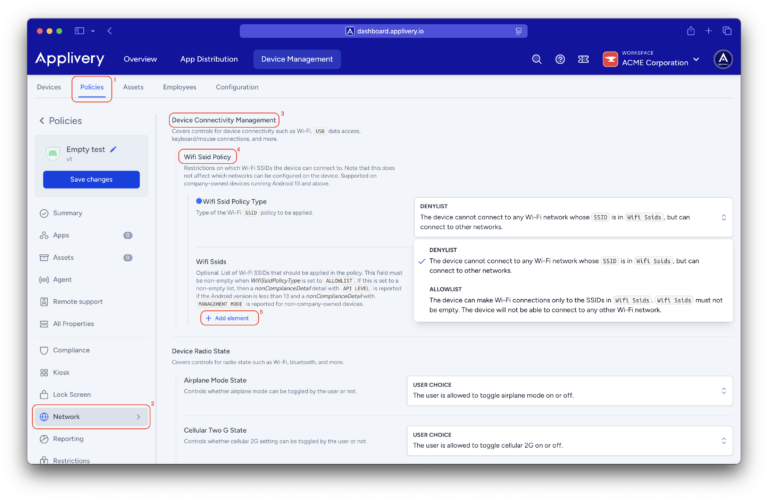
This simplifies your day-to-day, no more incident reports for dubious connections and no more security warnings to employees that nobody reads. You ensure compliance with regulations like ISO 27001 or GDPR and, most importantly, you give your team the freedom to work from anywhere with the peace of mind that they are operating within a perimeter that you have designed.
Implement your proactive security layer
Ultimately, this isn’t just about blocking a Wi-Fi network. It’s about shifting from a security posture based on hope to one built on clear, enforceable rules. Implementing an Allowlist is one of the smartest plays you can make: you close a massive door to external risks while simplifying your day-to-day management.
If you’re ready to implement this proactive security layer, you can dive into the technical details in our documentation to see exactly how the feature works. For a more guided approach, contact our team at Applivery to build your strategy with an expert, and we’ll help you design the perfect connectivity policy for your company.