Note that this is a premium feature that might not be available in your current plan.
Check the availability on our pricing page.
Customers can now manage their own storage regions in AWS S3. This tutorial will help you properly configure your custom storage region in AWS.
Step by step configuration #
Step 1 - Bucket creation #
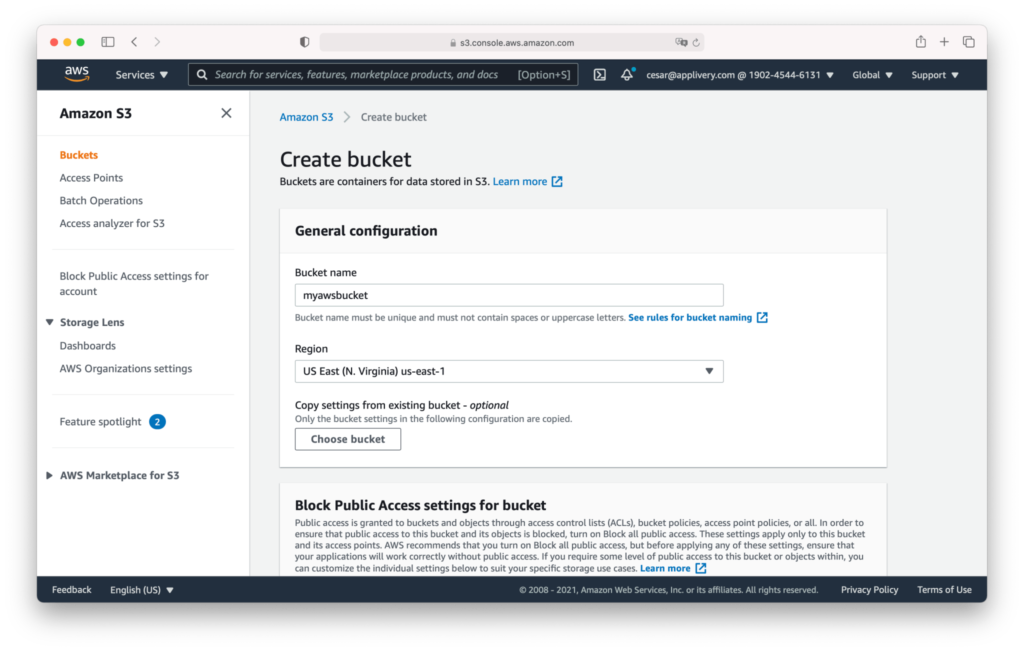
- Block public access to buckets and objects granted through new public buckets or access point policies.
- Block public and cross-account access to buckets and objects through any public bucket or access point policies.
- I acknowledge that the current settings might result in this bucket and the objects within becoming public.
Step 2 - Credentials configuration #
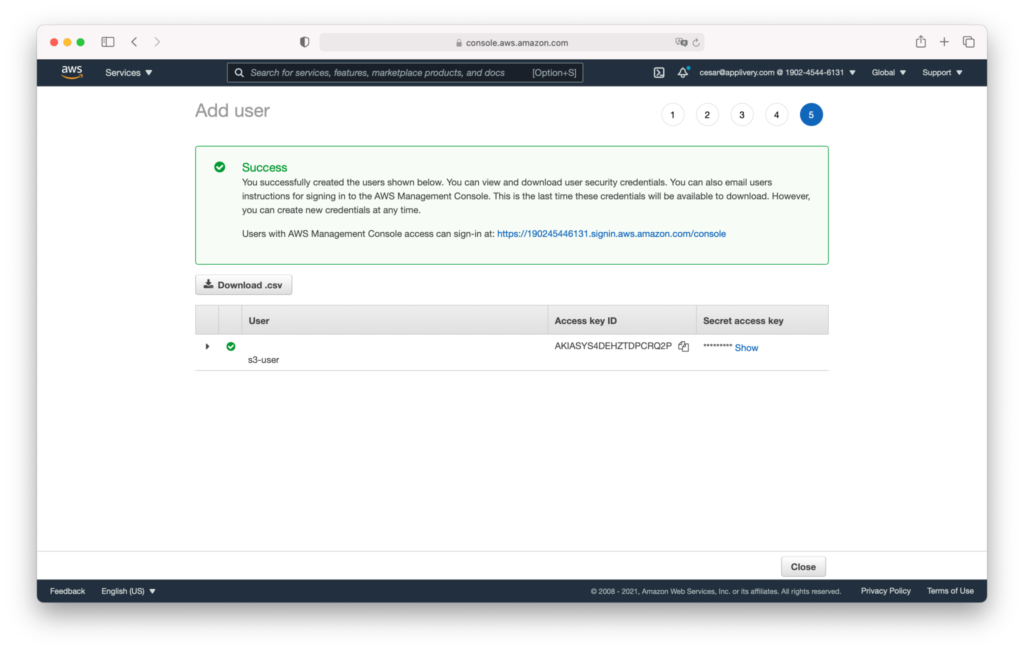
Step 3 - Grant permissions #
Now we have to grant some additional permissions to the new user. For this example, we will use the Inline AWS policies but as an alternative, you can create a new policy and attach it to the user.
Click on the new user and click Add inline policy under the Permissions tab. Use the {} JSON editor and enter the following AWS Policy:
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject",
"s3:DeleteObject",
"s3:GetBucketLocation",
"s3:PutObjectAcl"
],
"Resource": [
"arn:aws:s3:::mycustom-private-bucket",
"arn:aws:s3:::mycustom-private-bucket/*"
]
}
]
}
arn:aws:s3:::mycustom-private-bucket with the ARN of the bucket you created in the previous step. Step 4 - Configure your Storage Region in Applivery #
Now that the AWS configuration is done, you will have to go to your Workspace Settings > Storage section and click the + Create storage provider button.
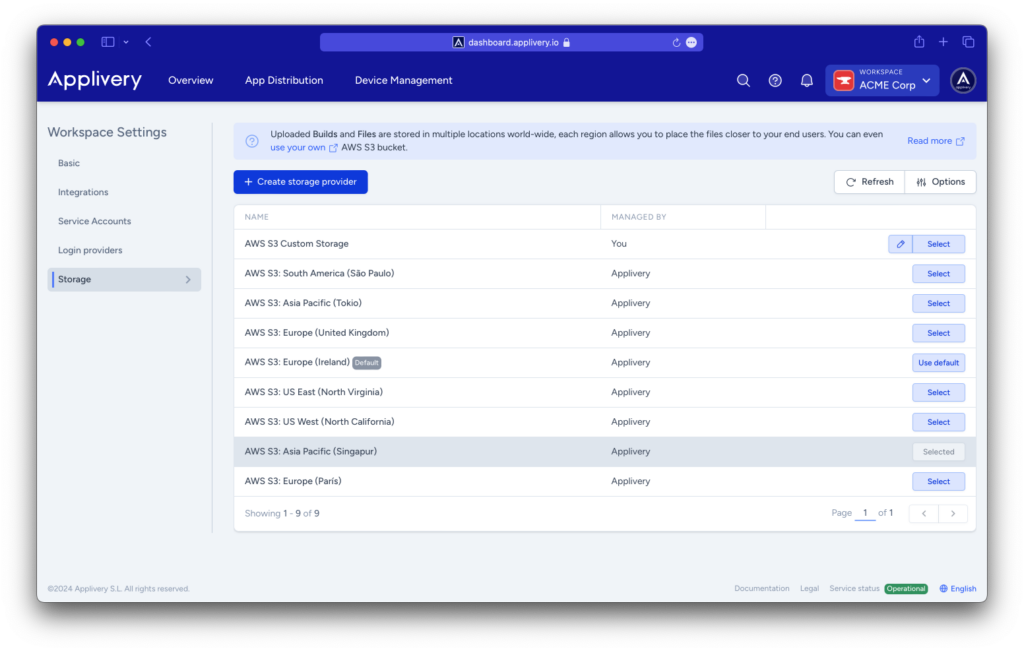
Complete the form with the information you generated in the AWS Console in the previous steps.

Step 5 - Select your new Storage Region #
- Workspace: The configuration will be applied to the entire workspace except. It will apply to all apps except those that already have a Custom Storage region configured. To do so, just click Select on this screen to enable it at the entire workspace level.
- App: The configuration will be applied just to this App, regardless of the workspace configuration. To do so, go to your App Settings > Advanced and Select the Storage provider you’d like.
Note that only the new builds uploaded will be stored in the new region. Previous ones will remain in the same place.
Disabling a Custom Storage Region #
You can disable a Custom Storage Region by clicking the Select button of the default storage region (Ireland).
Removing a Custom Storage Region #
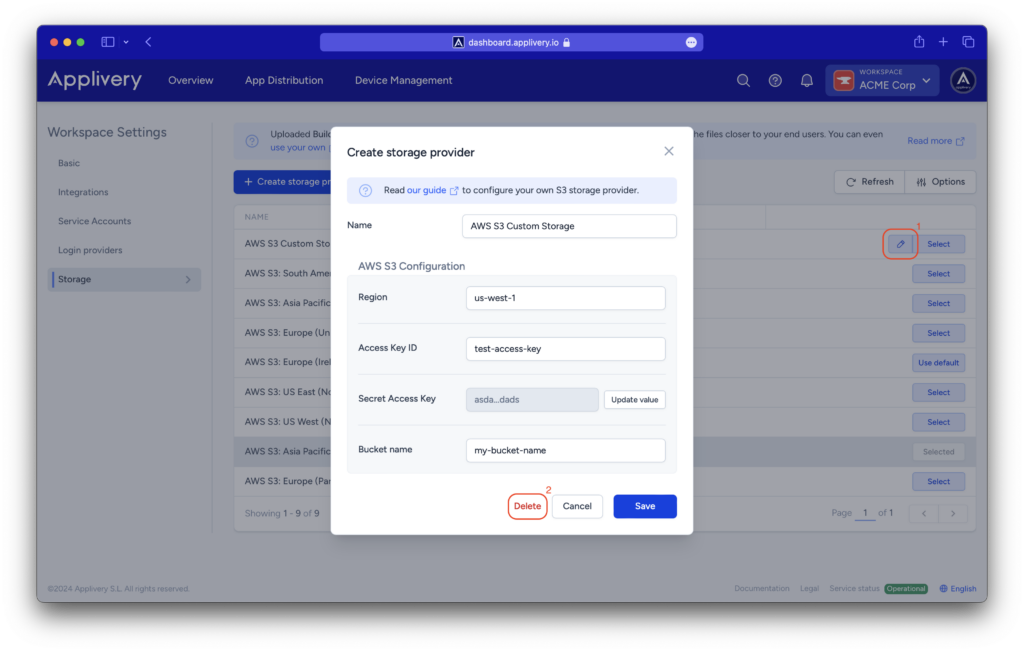
The builds uploaded to this storage will not be accessible anymore.